The Real Threats of Check and Email Fraud
In previous blog posts we’ve covered the threats posed by fraud, stark realities that can cause significant financial damage if not handled swiftly and with the right tools. Two common forms of these threats are check fraud and email fraud, both of which can exploit vulnerabilities in business operations and technology.
Check Fraud: A Case Study in Vigilance
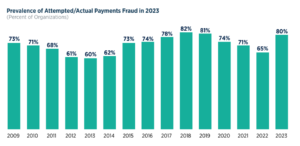
Payments fraud had been declining the past 3 years, down from a high of 82% in 2019, to 65% in 2022, but it’s back up to 80% in 2023. An important reminder for us to remain vigilant on our processes with payments.
Imagine managing the accounting department for a longstanding client, handling their bill payments seamlessly for years. Everything goes along fine until a police officer from Oregon contacts you about a suspicious check issued by your client’s business. This isn’t just any check; it bears your client’s remittance details but has been altered with a different payee and amount.
Then similar reports flood in from various states—Washington, Georgia, Maryland—all involving checks supposedly issued by your client but altered and duplicated for fraudulent gains. The sum at stake starts with smaller amounts but escalates to over $450,000!
Thanks to meticulous verification procedures and the implementation of Bill.com’s fraud prevention features like Positive Pay, disaster is averted. The client’s bank account details were safeguarded because only Bill.com’s routing and account numbers appear on checks, not the client’s actual account number. This simple measure ensured that none of the fraudulent checks could pass through unnoticed.
Because of collaboration across multiple police jurisdictions and the use of fraud prevention technology the severity of the threat posed by check washing and duplication was quickly handled. Without these defenses in place, the financial losses could have been catastrophic for the client.
Email Fraud: The Perils of Business Email Compromise (BEC)
In another scenario, an innocuous email request for a wire transfer of $1.4 million turns into a potential financial disaster for a business. As the trusted accounting department handling bill payments, you receive what appears to be a legitimate request. The email thread is convincing, with familiar employee names, project references, and attached documentation from the supposed vendor.
However, before proceeding with the wire transfer, your team follows strict protocols: written and verbal approval for all wire requests. It’s during this verbal confirmation that the fraud is realized. The person who supposedly requested the wire has no knowledge of it. Further investigation reveals a subtle but critical detail—the email address of the sender differs by just one letter from the legitimate domain name of the company.
This was no random phishing attempt; the fraudster had gained access to the company’s secure email system, allowing them to intercept ongoing conversations and insert their fraudulent request seamlessly. This type of attack, known as Business Email Compromise (BEC), preys on the trust and familiarity within the organization.
Lessons Learned and Strategies for Protection
Let these stories be a stern lesson for businesses of any size. Whether it’s the meticulous alteration and duplication of checks or the sophisticated infiltration of email systems, fraudsters are getting increasingly sophisticated in their methods. Here are some key takeaways to protect your business:
- Implement Strict Verification Procedures: Always verify unusual transactions or requests through multiple channels—phone calls to known numbers, face-to-face meetings if possible, and confirmations through other official channels.
- Use Technology Safeguards: Solutions like Bill.com’s Positive Pay for checks and advanced email security protocols can act as powerful deterrents against fraud. These technologies not only detect but can prevent fraudulent activities from progressing.
- Educate and Train Employees: Awareness is crucial. Train your staff to recognize phishing attempts, suspicious emails, and the importance of verifying any financial transactions. Regular security training can significantly reduce vulnerabilities.
- Enhance Email Security: Consider implementing multi-factor authentication (MFA) for email accounts, regularly update security software, and monitor for unusual activities or login attempts.
- Collaborate with Law Enforcement: In cases of fraud, collaboration with law enforcement agencies across jurisdictions can lead to faster resolution and mitigate potential losses and possibly protect the next victim.
Conclusion
Fraud in its various forms poses a serious threat to businesses, but with awareness, vigilance, and the right tools, you can significantly reduce your risk exposure. Whether it’s protecting your financial transactions with advanced fraud prevention technologies like Positive Pay or fortifying your email systems against BEC attacks, proactive measures are essential. Learn from these real-world examples and ensure your business is prepared to defend against the always evolving tactics of fraudsters. By doing so, you safeguard not only your finances but also your reputation and peace of mind.
Need help setting up Bill.com Positive Pay? Schedule a consultation today and we can help get you and your assets protected!







